Step-by-Step Activities
These detailed activities provide step-by-step suggestions for using the Security Cards in an educational or training context. The activities can be used "as is" or adapted and extended as needed. While the activities are phrased as academic lesson plans, they can be used in other contexts as well.
I. Sorting by Threat Importance
[html] [PDF, Example Systems PDF]
Have participants consider a specific system. With that system in mind, ask participants to consider each dimension independently and sort the cards within that dimension in order of how relevant and risky it is for the system overall. Within each dimension, what orderings are identified? Is there more than one reasonable ordering? Why?
II. Multi-Dimensions of Threat Discovery
[html] [PDF, Example Systems PDF]
Have participant consider a specific suste. With that system in mind and using the entire card deck, have participants explore card combinations from different dimensions to surface possible threats to the system. Which combinations of cards surface critical threats? Which surface surprising threats? Which threats are most relevant overall?
Extending the Activities
The activity ideas that follow may serve as starting points for lesson plans, extensions of the above activities, or follow-up assignments.
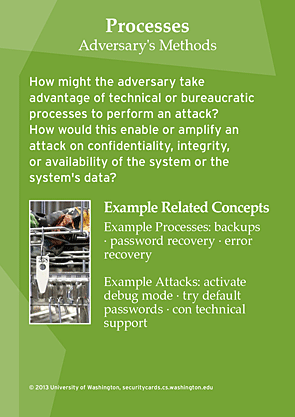
In general: Distribute the Security Cards to participants either in advance or at the beginning of the activity. Begin the activity by having participants look over the cards along all four dimensions (suits): Human Impact, Adversary's Motivations, Adversary's Resources, and Adversary's Methods. Encourage participants to read at least one card from each dimension, front and back.
For many of these activities, it is helpful if participants consider a specific system. If participants do not have a particular project or product to work with, we offer some suggestions for example systems.
Creating New Cards
Have participants consider a specific system. There are four template cards, one for each dimension. Given your system, your technology domain, your users, your business model, and other similar factors, what relevant card(s) do you wish were present that are missing? Create these cards (e.g., title, main text, examples, image concepts) using the included templates.
Current Events
Choose five cards from the deck. Make sure that cards come from at least three different dimensions. For each card, find a news article from within the last year that related to that card. Describe:
- The news event
- How the news event is an example of the ideas on the card. For instance, if the event is an attack, explain the attacker's motivation, what resources and/or methods the attacker used, or how the attack impacted human beings. Conversely, the event could be a thwarted attack or proactive defense; if so, similarly explain how the card is relevant to the event.
Expanding on Related Example Concepts
Notice that each of the cards contains some “Related Example Concepts” that broaden the context for the card. Select some cards to work with, making sure that the cards represent at least three different dimensions. For each card, consider the particular examples. Characterize these examples and identify reasons for why they might have been chosen. Then, think about other axes or characteristics that might be interesting or useful for identifying further examples.
Articulating the Unusual
Consider the Unusual cards for each dimension: Unusual Motivations, Unusual Resources, Unusual Methods, and Unusual Impacts. Generate some examples for each of the Unusual cards.
Advanced Topic: The Anatomy of Threats
Security threats can be conceptualized and analyzed using any number of frameworks. The Security Cards conceptualize security threats along four dimensions: Human Impact, Adversary's Motivations, Adversary's Resources, and Adversary's Methods. Is this a reasonable and complete way to conceptualize potential security threats? Why or why not? What other frameworks might be useful for analyzing security threats?
Advanced Topic: Accounting for Risk
Risk assessment is one way of taking into account the value of an asset and the likelihood that an adversary will attempt to carry out a threat and be successful in doing so. It can be calculated as follows:
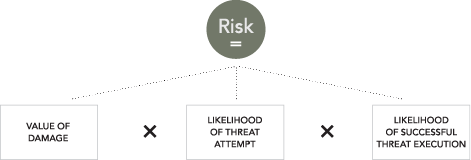
Create some additional cards for the deck to account for risk. Place each new security risk card into one of the four existing dimensions. If additional dimensions are needed to account for the new risk cards what would these dimensions be?
Advanced Topic: Considering Defense
Defenses are actions taken to counter a potential security threat. Defenses can take a variety of forms, and should be planned and executed in proportion to risks, costs, and payoffs. For any particular security threat, the question is: Given the anticipated risks (see the activity above) how many and what sorts of resources should be dedicated to addressing that threat? Create some additional cards for the deck to account for security defenses. Place each new security defense card into one of the four existing dimensions. If additional dimensions are needed to account for the new defense cards what would these dimensions be?